The aerospace industry can be looked at as a hi-rel subset of advanced embedded engineering, with the added pressure of a life-critical application space. Many of the trends rocking the consumer electronics, automotive, and industrial spaces also impact the mil/aero marketplace, from the Internet of Things to next-generation power electronics architectures. Another issue roiling the electronics industry is security, especially cybersecurity and protecting electronics systems from tampering and hacking.
The high level of electronics integration empowering the next generation of advanced aircraft must deal with the security and cyberwarfare dangers that exist. As Cloud-based systems and other connected technologies become more and more a part of avionics, engineers must address the potential risks threatening avionics. In this article we reached out to several companies in the avionics space, to get a real-time snapshot of the state of the industry.
An Expanded Risk Environment
For example, “Connected Aircraft” are replacing manual upload of avionics systems, such as Flight Management Navigation and Terrain database updates with wireless datalinks (SATCOM, WiFi, 4/5G). This creates potential for unauthorized access from a malicious player. Avionics architectures that used point-to-point connections, such as ARINC 429, are being phased out in favour of networked-based systems which are fundamentally open access.
Cybersecurity was once a software-only application space, with issues ranging from password management to back-door access through software exploits or simple holes in the code. Now security is becoming a hardware/software solution, manifested in devices like single-board computers (SBCs) with secure/trusted boot mechanisms, security features built into operating systems and board support packages.
The keys to the kingdom are also being protected now, with security of Data-In-Transit and Data-At-Rest, with certification processes compliant with ISO and DO-326A, along with techniques like penetration testing and white-hat hacking testing. Trusted Computing and Secure boot mechanisms use devices like Trusted Platform Modules (TPMs).
TPMs authenticate the executable code running on the SBC using Secure Hash Algorithms (SHAs), which produce unique encrypted codes for executable files when installed on an embedded computing platform. In addition, network security mechanisms such as MACsec, IPsec ,and Transport Layer Security (TLS) provide additional protection, with Security of Data-At-Rest provided by dual-layer FIPS140-2 encryption for networked attached storage.
CoreAVI image.
CoreAVI
Core Avionics & Industrial (CoreAVI) is a leading supplier of real-time safety-critical graphics and compute drivers, COTS Hardware IP, and embedded graphics processors (https://www.coreavi.com/). Deployed on most major commercial and military platforms, CoreAVI drivers have been certified to DO-178C/ED-12C up to and including DAL A, and are aligned with the Future Airborne Capability Environment (FACE) Technical Standards.
We reached out to Michael Pyne, director of Strategic Accounts & Solutions Architect for CoreAVI. He pointed out that the company agrees with the challenges laid out in the ICAO Assembly Resolution A40-10 on Addressing Cybersecurity in Civil Aviation, in that threats are increasing, vulnerabilities are expanding, and that a holistic approach to solutions for security problems is required.
According to Pyne, CoreAVI is particularly sensitive to the relationship between safety criticality/certification and cybersecurity, especially in an aviation world that is increasingly adopting an Internet-of-Things approach in the cockpit, with things such as WiFi-enabled Electronic Flight Bags, Off Boarding Systems, and other connected functionalities.
As Pyne points out, “CoreAVI is applying its robust safety critical processes, for system and software development, integration, and validation, to cybersecurity requirements. We are working with our customers to augment our development process discipline and rigor with cyber-threat assessment modeling and cyber-threat testing approaches.”
He continued, “This environment is being guided by previous work with DOD standards like CNSS 1253 and FIPS 140-2, and evolving directives such as FAA ESSA Section 2111. CoreAVI’s exhaustive Failure Modes & Effects Analysis (FMEA) process is being enhanced with cyber-security considerations such as confidentiality, availability, and integrity, as well as impact assessments such as catastrophic, critical, marginal, and negligible.”
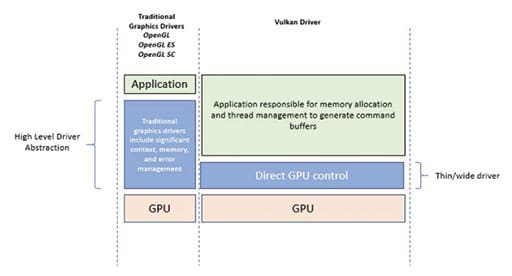
CoreAVI’s products ensure graphics presented to operators in today’s most sophisticated cockpits are protected to the highest levels of safety criticality (Design Assurance Level A). THese solutions address heterogeneous computing architectures (CPUs + GPUs) for things like artificial intelligence, machine learning and autonomous flight in next-generation aircraft cockpits. CoreAVI recently invested in Safety Critical Vulkan (a Khronos group-sponsored GPU acceleration API for modern CPUs/GPUs). Vulkan’s Safety Critical compute and graphics API is a natural starting point for cybersecure solutions in the cockpit (Figure 1).


When asked about the security landscape going forward, Pyne mused, “Advances in avionics systems are providing the roadmap to where the threats are going to come from, and communication systems like CPDLC are becoming more prevalent. So we would expect to see threats via datalink hacks to become more common. Air Traffic Controller communications are becoming more automated, taking the man out of the loop more and more, which poses additional cyber threat challenges.”
“Off-boarding tools used for flight pre-planning and maintenance reporting may also present new threat opportunities. Pilots and maintainers using these off-boarding devices in international operations further complicates security measures. CoreAVI expects to see an increase in ‘economic’ motivations for cyber threats as opposed to terrorism or mischief motivations.”
ENSCO Avionics
ENSCO Avionics (https://www.ensco.com/) develops sophisticated airborne systems for the aerospace industry to meet DO-178C/ED-12, DO-254/ED-80, DO-278A/ED-109, DO-326A, and military standards for manned and unmanned systems. The company’s IData development platform aligns with the FACE Technical Standard, established by The Open Group Future Airborne Capability Environment Consortium.
Defining an open avionics environment for all military airborne platform types, the FACE Consortium is a vendor-neutral forum that provides standardized approaches for using open standards with avionics systems, developing and consolidating the open standards, best practices, guidance documents and business models needed.
We spoke with Robert Sanders, vice president of ENSCO Avionics, on the security issue. He explained to us how they see the cybersecurity landscape as very broad, encapsulating software and hardware domains ranging from Operational (OT) and Information Technologies, (IT) to Physical Access, to assets and equipment. Robert observed that It seems that many of the recent Cybersecurity threats perceived are focused on IT’s response to hacker attacks on company and government servers and domains, to gain access to protected or sensitive data.
In the area of avionics systems, the company is also concerned about risks to aircraft that result from malicious passenger access to embedded software and systems within the aircraft boundary, or cyberattacks on Air Traffic Control systems. The ability to gain access to on-board systems like In-Flight Entertainment systems as a means to interact maliciously with safety-critical systems, like Flight and Engine Controls, is a real Cybersecurity threat to Avionics systems. However, compliance with Airworthiness Safety criteria helps limit or potentially eliminate broad opportunities to gain access to higher criticality subsystems from lower criticality subsystems.
The reality of the Cybersecurity threat to Aircraft today and in the future is sourced from a more diverse set of Aircraft interaction risk domains. The threats potentially start very early in the safety-critical hardware and software design processes, with introduction of malicious function. Threats extend to real-time interaction with air traffic control and navigation systems by injecting misleading or false data throughout the mission envelope. Even aircraft maintenance operations performed by maintenance organizations are a risk point, where aircraft access controls may be challenging to enforce.
In the case of Unmanned Aircraft Systems (UAS) and Urban Air Mobility (UAM) initiatives, it is reasonable to assume there will soon be a major transformation in National Air Space (NAS) Safety and Security. It’s a fair assumption that a higher degree of network and vehicle interconnectivity and control complexity will be required to ensure the future NAS remains safe and secure. However, higher degrees of connectivity may increase aircraft and infrastructure vulnerability to cyberwarfare tactics and exposure to cybersecurity threats.
When asked about what the company is doing to address these concerns, Sanders said, “ENSCO has been supporting corporate and government Cybersecurity objectives for years throughout the Physical Access and IT domains, and aggressively pursued and achieved compliance with the Defense Federal Acquisition Regulation Supplement (DFARS) 800.171, which is Cybersecurity criteria mandated for Government Contractors.”
“DFARS 800.171 ensures that ENSCO’s internal Information Technology Systems are consistent with DoD Cybersecurity standards. This strategic compliance ensures that Safety-Critical Avionics HW and SW life cycle activities performed on systems within the ENSCO domain and facilities are secure from Cybersecurity threats for both customer and internal programs and data.”
Sanders further explained, “ENSCO has been providing Cybersecurity compliance services to the US Government and Aerospace Customer facilities, servers, networks, and system software for years, with NIST compliance assessments and accreditation for both Customer and Government organizations. For Commercial Avionics, industry guidance for mitigation of Cybersecurity risks is available from RTCA in DO-326A Airworthiness Security Process Specification, DO-356A Airworthiness Security Methods and Considerations, and DO-355 Information Security Guidance for Continuing Airworthiness.”
“This “Airworthiness Security” guidance was prepared by a Special Committee (SC-216) comprised of industry expert volunteers, and ENSCO Avionics has been a contributing member of the SC-216 special committee as the guidelines were developed. In addition to involvement in Aerospace Industry Cybersecurity Working Groups, ENSCO has initiated internal R&D investigations into Cybersecurity domain knowledge, Tools, and Design Assurance Strategies for Airworthiness Security compliance.”

Sanders continued, “Today, ENSCO Avionics’ internal HW and SW development activities are performed with built-in Airworthiness Security compliance in mind. With appropriate diligence and continued focus on the full Cybersecurity Risk landscape, we keep ahead of daily Cybersecurity threats to our business and products. ENSCO has mature security processes and enforcement mechanisms in place to ensure secure special test/lab facilities, software and hardware development environments and verification environments (Figure 2).”
ENSCO states that the most significant cybersecurity threats will likely emerge from transformation of the National Air Space to accommodate next-generation vehicles and systems. It is a technological imperative to leverage current and emerging advanced technologies, to ensure superior computing capabilities needed to manage the complexity of the diverse aircraft types, functions and platforms involved.
Advanced technologies like multi-core processors, system-on-a-chip, wireless/WiFi, and virtual networks into Aircraft tends to disrupt Airworthiness Safety and Security, meaning that safety, reliability, and security could degrade based on the unique impact of their specific integration and use. It’s more than speculative to believe that the complex interactions between UAS/UAM market forces, diverse Aircraft types/capabilities and technology demands will increase Cybersecurity risks and introduce new, unforeseen threats.
Curtiss-Wright
Curtiss-Wright’s (https://www.curtisswright.com/) participation in the aviation industry goes as far back as the industry itself, from the Wright brothers’s invention of the aircraft to today. From Curtiss-Wright’s sensor and data recording products to monitor and communicate vital data on conditions within and surrounding the aircraft, to fire-protection systems, to enhanced cockpit controls and mechanical actuation systems.
We were able to catch up with Paul Hart, chief technology officer at Curtiss-Wright. When it comes to cyberware dangers do you see threatening avionics, Hart feels that one of the dangers stems from traditional data exchanges between an aircraft and the aircraft system on the ground. For example, manual uploading of navigation databases is now being replaced with wireless connectivity.
In that scenario, an aircraft arrives at the gate, flags that it needs to update its database, and the maintenance control center or the airline operation control center will automatically trigger an upload. The danger there is that without cybersecurity in that link, a malicious player could intercept that transmission, and maybe perhaps spoof a broadcast onto the aircraft. So a result of aircraft becoming more connected is that it introduces a number of potential vulnerabilities, especially on the aircraft with WiFi domains.
Passenger-in-flight entertainment is using wifi, but the pilots are using it too, with tablets that connect to the aircraft control system. They use them to pull up parameters from outside, air temperature, and pitot-static data, among others, to calculate takeoff performances for example, or weight and balance calculations. Now normally these are protected by Wireless Protection Access encryption methods, but there have been cases where these have been breached, and there is potential to connect across the different wifi domains on an aircraft.
A military aircraft is traditionally connected with a MIL-STD-1553 bus, and commercial aircraft avionics and sensors have all been connected together using ARINC 429 point-to-point data buses. These are all giving way to having CAN- or ethernet-based networks, which are fundamentally open architectures designed for plug and play in the commercial world. By connecting a network that’s onboard the aircraft to a netbook that’s wifi enabled, you have a couple of areas where there’s exposure to cyber risks.
Hart elaborated, “If an airline has decided they’re going to update all of the flight management system databases every 28 days, which is the mandatory requirement, using some wireless connectivity, a malicious player could hack into that system, and could disrupt the uploads for those databases for the whole fleet of aircraft. So there’s a potential risk that would encompass a large number of aircraft.”
When asked about the growing hardware-based security aspect, Hart observed that a lot of processes now come with trusted platform modules, so the objective is to authenticate the code to ensure there’s no malware. Prior to code being executed, the trusted platform module will run a secure hash algorithm on it. If it comes up with a different answer, something’s tampered with that code. What’s happening now is more and more people are looking to use trusted platform modules or trust zones so that there is a secure boot process.”
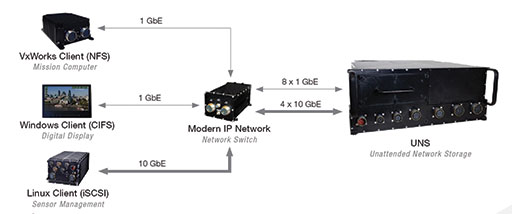
“For example, our UNS, Unattended Network Storage, is a rugged network attached storage system that supports standard network storage protocols through four 10 GbE and eight 1 GbE ports (Figure 3). Trusted to protect critical data-at-rest, the UNS incorporates Top Secret/Sensitive Compartmented Information encryption for unattended applications.”
“For network security, you embed in IPSec, MACsec, or Transport Layer Security, which essentially creates a session key between the source and the destination IP addresses. And the keys are sent separately so that anyone that wants to break and inspect in that link either by physically plugging into a network switch or joining a WiFi network, would be unable to intercept those messages.”
“So use of crypto processes, Transport Layer Security, network security are becoming more and more widespread and necessary. Curtiss-Wright computer systems are available fitted with an Intel tracker platform module, and the ruggedized computers out of the company’s Salt Lake Parvus facility are now fitted with trusted platform modules. This capability extends to our dedicated ultra-small form-factor mission computers.”
Hart continued, “Customers need to start specifying cyber-secure features when they buy an SBC, and make sure it comes with a trusted boot, or some form of trust zone or trusted platform module embedded on the board. Are you able to authenticate the code using an accredited secure hash algorithm? That way you can guarantee that if your code has been tampered with, you can then have a policy that will prevent it from being executed.”
“The next thing is encryption, and we have FIPS 140-2 layer encryption, where you have full drive software encryption and full drive hardware encryption. It’s kind of like two bits of Swiss cheese. If you overlay them the chances are you have closed up all the holes. So by having the data at rest, anything that’s stored on a hard drive or removable media have encryption layers built in to show it meets an accredited recognized standards such as FIPS 140-2, and also the grade, there’s grades one to four and generally grades two and above would be acceptable for aerospace.”
“From the regulatory aspects in terms of avionics, the FAA has issued a policy statement on cybersecurity and the ASA is putting two pieces of legislation through the European commission right now, which will be mandatory in the next few months to deal with aircraft cybersecurity and another one to deal with the management of information security risks. Now in all three cases, where it boils down to the avionics, there is a document called DO-326A on aviation cyber-security airworthiness certification, and there are some companion documents that go with it. They’re known as the DO-326 set on compliance in making the assessments of cybersecurity and building and testing out the mitigation strategies. Cybersecurity is a constantly moving target and we have to be vigilant.”
Daedalean AI
Artificial Intelligence (AI) is a rapidly-advancing disruptive technology that is now beginning to address the aviation space. Daedalean (https://www.daedalean.ai/) is a Zürich-based startup with a mission to create a certified airworthy autopilot based on AI that can pass the exams for human pilots. The company recently signed an agreement with Honeywell on joint testing and technological partnership in developing solutions for autonomous takeoff, landing, and GPS-independent navigation and collision avoidance for GA aircraft and electric vertical takeoff and landing vehicles (eVTOL).
To talk about cybersecurity in AI-based systems, we spoke with Luuk van Dijk, founder and CEO of Daedalean. On the security and cyber warfare dangers threatening avionics, the company’s position is that there is a clear trend to the more connected aircraft, and every connection with the outside world is an attack vector. The more external data paths you have into and out of the aircraft, the more possible exposed surface you have for cyber-attacks.
Any data that is critical for flight planning and for technical navigation decisions and collision avoidance decisions, any piece of data becomes part of a safety-critical path of control. As van Dijk points out, “GPS, for example, can be notoriously spoofed or jammed actually. It’s routinely jammed over whole parts of the United States to practice what things would look like without GPS for the U.S. military. You can buy a jammer on Alibaba for a couple of bucks to disable it in a small circle around you. That has implications for the safety of systems that rely on these signals to be there.”
“No serious aircraft critically relies on GPS, but still pilots might become reliant on it as a matter of habit, and especially in general aviation. If you plan your own path, you sort of expect your glass cockpit to display accurately where you are roughly, and you’re supposed to be able to deal with it if it’s not there. But the more reliable these things are in daily life, the more surprising it is and the more risky it is if it’s suddenly not there. For example, an ILS system does not use GPS to guide you to the ground, because it’s known to be not sufficiently reliable for those last meters of altitude.”
van Dijk stressed, “But then the ILS beam itself is a radio beam that you could spoof and hack. It would probably be obvious to all involved if this was going on. But the more avionics you have that become routine part of how the plane flies, the more you have to keep these attack vectors in mind.
“In the case of our product roadmap, our intent is to replace how a human pilot functions with a system that outperforms the human. We deliberately started in VFR, because in visual flight rules you can fly around without too many dependencies and uncontrolled space, and in specifically that gives us a chance to start without having to worry about the data links. For example, one of the systems we have developed is as a human pilot who’s flying on visual rules, your GPS is completely optional. You look out the window and you’re supposed to be able to navigate a rough map of landmarks.”
“That’s actually the system we replicated. Our computer vision system can just look out the window, actually it looks out of the camera that’s mounted somewhere on the aircraft, and it recognizes really big things like mountains and coastlines and big roads, and it can use that to fly from A to B without a GPS. We took the human performance there as a baseline. First thing you have is your eyes to see where you are. The second thing you have your eyes for is to see where you can land, which is also very important if you’re flying. And the third thing you use your eyes for in VFR is for collision avoidance to see all the cooperative and non-cooperative traffic for which you’re also supposed to use your eyes in VFR.”
“An interesting consideration there was exactly that we don’t want to depend on external data. You have lots of collision avoidance systems that assume that the other party has a transponder and that’s great. In the U.S. that’s currently rolled out as mandatory. So that means that most things that fly will actually be broadcasting a signal saying, “I am here and I am this and I’m going that way,” and that’s as far as they’re reliable. But it also introduces a dependency, and if that transponder is gone, you’re not allowed to fly into them just because they have their transponder off.”
“A human can fly a Piper Cub aircraft with almost no instruments perfectly fine by just looking out the window. And that is… I don’t know if you’ve ever flown in one, but there’s a steel bar in your hands with steel cables going over pulleys. There’s no need to switch off your telephones and transmitting equipment because there’s nothing on board remotely electronic to interfere with. It’s very hard to spoof a mountain range. If you want to disorient a pilot who is looking out the window, then provided the vision is good, the visibility is good, it’s going to be hard to beat that. So that’s exactly one of the things we’re trying to build in that level of resilience and reliability, without depending on external data.”
“When it comes to security, one of the things we do is that we don’t actually learn online. Once the system is deployed in the aircraft, you’re not going to have it magically learn new things without your supervision. It’s fine to collect the data, send the data back to the lab, train a new version of your algorithm in the lab, but then you reassert and you reassure all the design and performance aspects before you roll it out.”
van Dijk concluded, “We have all the safety critical decision making-capability on board. We can vet all external data sources against something that we can see for ourselves, which is what the human pilot’s also expected to do. So if somebody spoofs the GPS or if somebody falsified the maps, we can look out the window and say, “I’m quite sure I’m here and not somewhere else,” or “I’m quite sure that the whole mountain range actually is still in the same place.”
Looking forward
The aviation industry has to pay attention to a large variety of threats, and cybersecurity is only one aspect of the whole safety and security solution set. However, with the high levels of connectivity and processing functionality involved in avionics, ensuring system and code security is a paramount concern. Getting a handle on the cybersecurity solutions available and implementing them effectively will go far to ensuring the security of your aircraft.
